Product security flaw, vulnerability, and remediation
When it comes to management of any issues which may implicate any iStorage product with a flaw, vulnerability, or any other logical condition which may implicate the security objectives of assured CIA+A (Confidentiality, Integrity, and Availability) iStorage are committed to follow a robust set of processes, and our mission statement to apply countermeasures and mitigations to secure our products.
Mission Statement
iStorage follow a proactive operational set of practices with the firm objective of maintaining a secure and robust profile of our products, by discovering, and applying prioritised flaw and vulnerability remediation processes to prevent the manifestation of security exposures, instability, or conditions which may be manipulated directly, or indirectly to compromise a system, asset or iStorage product.
In the first instance, this is achieved by the application of a set of operational objectives, under an established iStorage SDLC (Secure Development Lifecycle) at all levels of development, and, where required to manage a robust process of flaw and vulnerability remediation and management to mitigate, and to underpin a secure product range – including:
Risk: Flaw and vulnerability management has become increasingly important factor for all organisations over the last decade, driven by the high number of high-profile global targeted cyber-attacks, system compromises, and associated loss of sensitive data assets, implicating Confidentiality, Integrity, and Availability (CIA). Therefore, iStorage see flaw and vulnerability management as high-priority when it comes to their products, and apply and follow robust practices and procedures to assure that any actual, or suspected flaw, vulnerability, or security exposures are addressed as soon as they are discovered, or reported to assure that all iStorage products in operational use are secured and protected from any form of cyber-attack or compromise which could exposure client’s data assets, or otherwise cause a denial of service to an iStorage product. Internal to iStorage this is managed by following strict guidelines to accommodate the following security objectives:
Design: In this phase, iStorage apply best industry security practices as part of their developed in-house SDLC (Secure Development Lifecycle) concerned with the creation of source code, runtime code, and all applicable manufacturing practices in support of developing secure and stable code, and robust products.
Development: Again, the aspect of development follows the same practices as those inherent to the design phase and the direction of the SDLC. However, in this phase the development team security operating procedure (SyOp) is also applied to direct the teams approach by underpinning with a set of mandated operational instructions and control objectives based on the ISO/IEC 27001, and many other industry best security practices.
Deployment: Under the iStorage SDLC, the deployment phase requires that complete verification and process is applied to ensure that all products are operating as expected, and are supportive of the objective to deliver secure, robust and stable products into the delivery chain of iStorage for business users and clients alike.
Distribution: iStorage ensure that their products are distributed to their end clients in a form which supports the Integrity of their products (CIA). For this reason, and to mitigate the potential of tampering, all products are sealed in secure packaging along with the application of tamper proof seals.
Upgrade: As part of the SDLC, on the rare occasion where a flaw or vulnerability is discovered which directly, or indirectly affects the security, stability, or operability of any iStorage product, immediate remediation action is taken to investigate, evaluate and to mitigate the discovery as appropriate.
Maintenance: The iStorage development team carry out regular maintenance against all source code and products to ensure they are concurrent with any newly published security alerts, notification or vendor updates as are applicable to their product base; or any other associated party who support iStorage to ensure they are always up to date with the latest vulnerability notifications.
Flaw and vulnerability remediation and reporting
The iStorage technical support team (TS) is responsible for maintaining secure products by ensuring that any discovered or reported flaws, vulnerabilities, or other technical issues which may have impact on their product range are dealt with as a matter of priority as soon as they become known. This is underpinned by the many robust processes which iStorage deploy into their product and manufacturer SDLC as shown above.
Response: iStorage have developed a set or processes and protocols which they apply to respond to any adverse reports which implicate their product range. This is achieved by dedicated iStorage technical support teams who manage the receipt of any such notifications, which are then followed up with internal evaluation of the observation. The process will then follow a conjoined set of high-level processes, applied by technical support teams to Manage, Coordinate, Evaluate, Verify, Prioritise, Remediate, as shown at Fig 1 below:
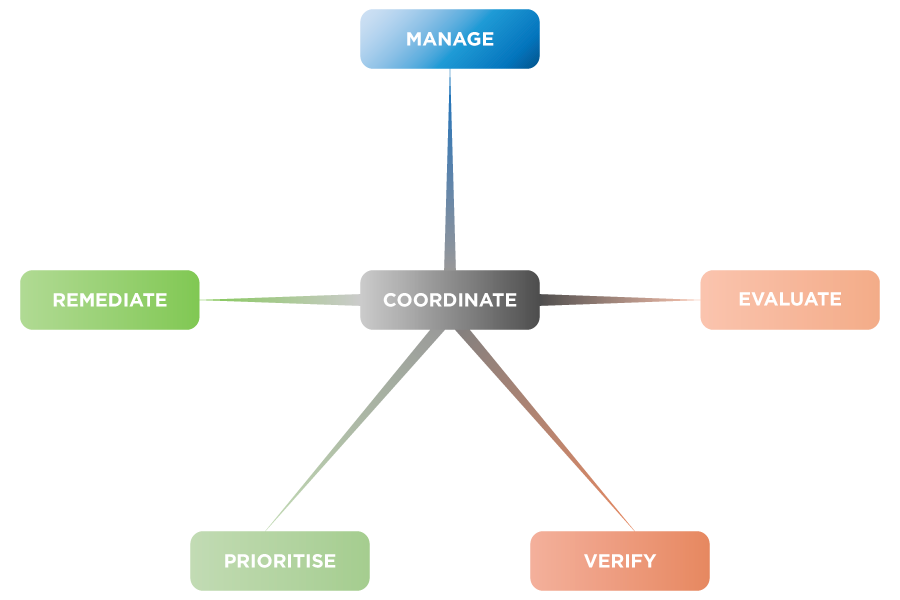
Fig 1: High-level flaw / vulnerability reaction life cycle.
This process is in place to assure that all products which could be exposed to allow an unauthorised actor to compromise the Confidentially, Integrity or Availability, are reacted to as a matter of high-priority by iStorage technical support teams who will quickly:
Reporting or obtaining support for a suspected flaw, vulnerability or security exposure
Any user or organisations who suspect that any iStorage product may have a flaw, vulnerability, security exposure, or some other condition which may implicate its stable operability should contact the iStorage technical support team as soon as possible.
Under this same process, iStorage also welcome reports from independent researchers, security consultants, industry organisations, vendors, customers, and other sources concerned with product security or stability. To submit a report takes minimal effort, and may be done by either contacting iStorage by email, or on one of their contact telephone numbers as shown below:
| Telephone contact: | E-mail: | |
|---|---|---|
| +44 (0) 20 8991 6260 | support@istorage-uk.com | |
| +44 (0) 20 8991 6283 | ||
| +44 (0) 20 8991 6265 |
Response to notifications
iStorage take all reports very seriously, and upon receipt of any notification relating to a flaw, vulnerability, or any other observation relating to product security, stability, or operability, we will follow the high-level process as shown in Fig 2 below:

Fig 2: Flaw and vulnerability reporting process
Our security commitment
iStorage is committed to responding to all received reports and notifications as a matter of urgency, and where required will take direct action to mitigate the flaw, vulnerability, or observation as a matter of high-priority to ensure all our products are always secure.
| Device | Firmware version | Security flaw |
|---|---|---|
| datAshur | v1.2 | No flaws found or reported |
| datAshur PRO | v1.9 v1.11 |
No flaws found or reported |
| datAshur Personal | v2.1 | No flaws found or reported |
| datAshur Personal2 | v1.9 | No flaws found or reported |
| diskAshur 2 | v1.2 v1.4 v1.6 |
No flaws found or reported |
| diskAshur PRO2 | v1.2 v1.4 v1.6 |
No flaws found or reported |
| diskAshur DT2 | v1.2 v1.4 v1.6 |
No flaws found or reported |
Note: this table will update within 7 days of a new firmware release